As you probably have already noticed, the number of VPN providers has grown massively in the recent years, and you can now stumble on ads for VPN subscriptions on every corner of the Internet. Of course, not all of these providers are equal in terms of quality of service, security or privacy. At the contrary, some of them falsely claim to have a zero-log policy or to even protect you from malicious actors.
Having said that, using a public VPN service is not necessarily a bad idea if you choose it correctly. It's a matter of trust after all. Who do you trust the most for keeping your traffic private, your ISP, or a carefully selected VPN provider? (I said carefully here because you have a larger number of VPN providers on the market than ISPs available where you live).
If you trust your VPN provider, you get in theory a higher degree of online privacy by proxying your connections through it (even if, as of today, nothing can fully replace Tor). But what about security? From a theoretical standpoint once again, TLS is well enough to guarantee the security of your online activity. And thanks to projects like Let's Encrypt, most websites are accessible via HTTPS these days.
So, using a VPN doesn't give you a better security? Well, in practice, it's not that simple, and for one simple reason: there are lots of misconfigured web servers out there! And it is actually the reason I wanted to write this blog post. To be more precise, it is this Twitter thread which made me realise that even experienced information security people can miss this point:
"Please stop with your misinformation campaign. VPNs are completely unnecessary to protect someone in this scenario, https works just fine." @SchmiegSophie
Sophie is right here, HTTPS works fine, but only when properly configured. As a matter of fact, I use an online accounting web application called Bullet for the needs of my company. When I try to log into my Bullet account, here is what happens:
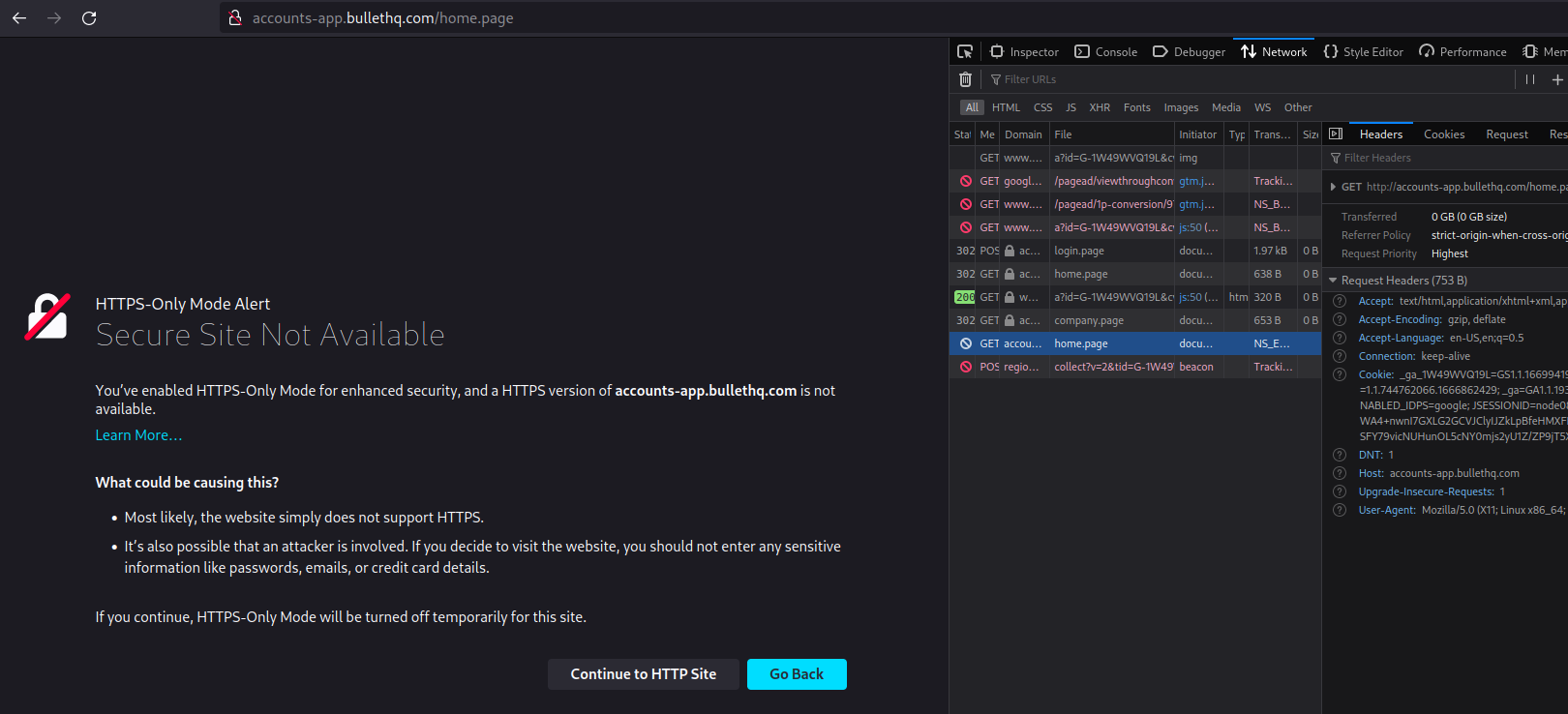
As you can see, I am redirected to an HTTP page, leaking the session cookie
because it is not marked as Secure. I let the company
know about this security issue months ago but to this date, they still haven't
taken any actions to fix it, hence the public disclosure here.
This category of issues is unfortunately quite common. Just the other day, the same thing happened to me once again on the Help Desk tool of a cloud provider specialised in Healthcare Data Solutions (HDS). It goes without saying that impersonating an account used to request actions on production systems is something not desired... If I were to be connected to a public Wi-Fi while triggering one of those improper HTTP redirects, a malicious actor on the same network could have stolen my session token, and indeed, tunnelling my network traffic using a VPN is a way to prevent it.
Another less costly way to prevent your browser from leaking personal data, including session cookies, is to turn on the HTTPS-only mode of your web browser as I did with Firefox. The result is the one of the above screenshot: Firefox warns you when plaintext data is about to be sent.
To conclude, the decision to use or not a VPN is yours, and my intention was solely to help you weight the pros and cons on that matter. If you think a VPN can fit your needs, I recommend Mullvad VPN (this is my personal opinion, not a sponsor) for the following main reasons: EU-based company, diskless infrastructure, post-quantum cryptography, open-source software without trackers (and written in Rust!), supporting open-source projects such as Qubes OS, and transparent security audit reports.